What is Security Validation?
The concept of security validation covers all
adversarial testing tactics that mimic real cyber-attacks.
By safely attacking their environment,
organizations can verify how efficient their detection
and response mechanisms are. Security validation
began as penetration testing but keeps evolving to
match cyber-attackers' enhanced capabilities.
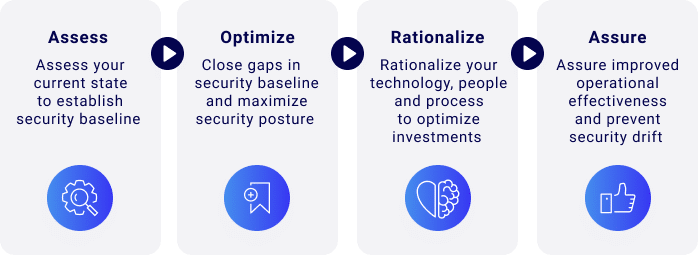
Uses of Security Validation
There is no end to the number of ways continuous security
validation can be beneficial including: optimizing security
controls, SIEM validation, future-proof & compliance-ready security
posture management, due diligence for M&A, efficient
prioritizing of vulnerability patching, checking employees
security awareness, the list goes on.

